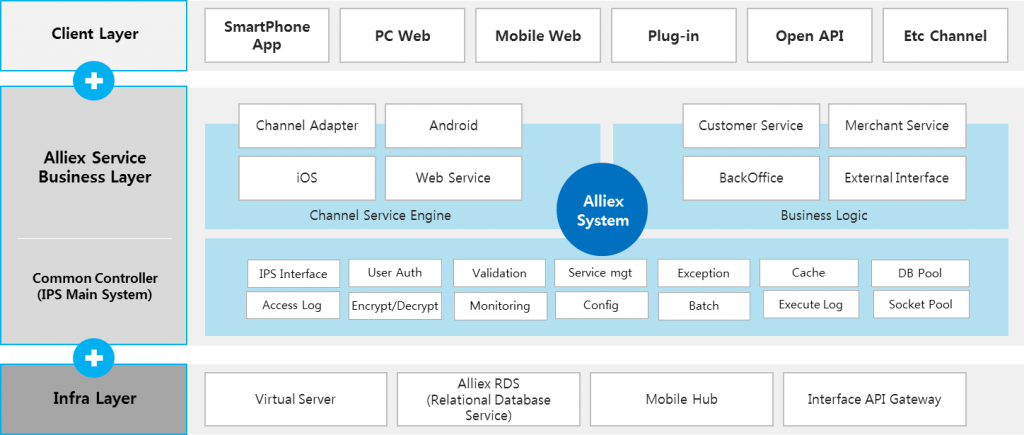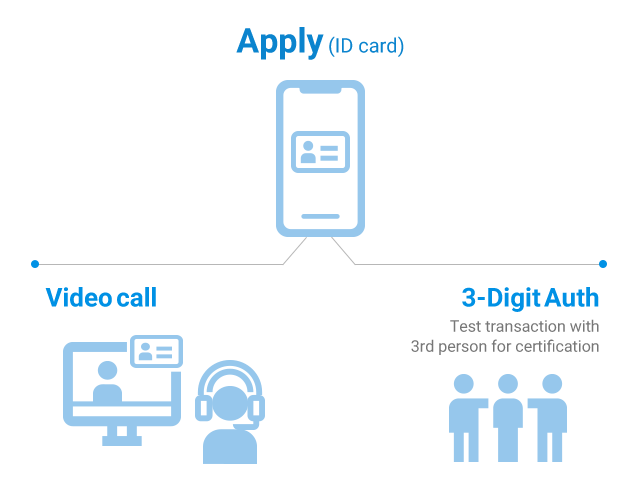
Users can now open accounts, issue cards, and subscribe to financial services without visiting a financial institution.
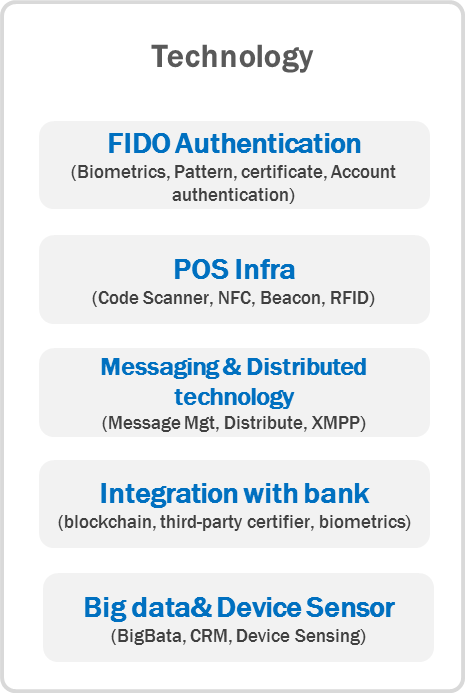
Non-facing financial services that satisfy both authentication, security and convenience are based on high-level technology.
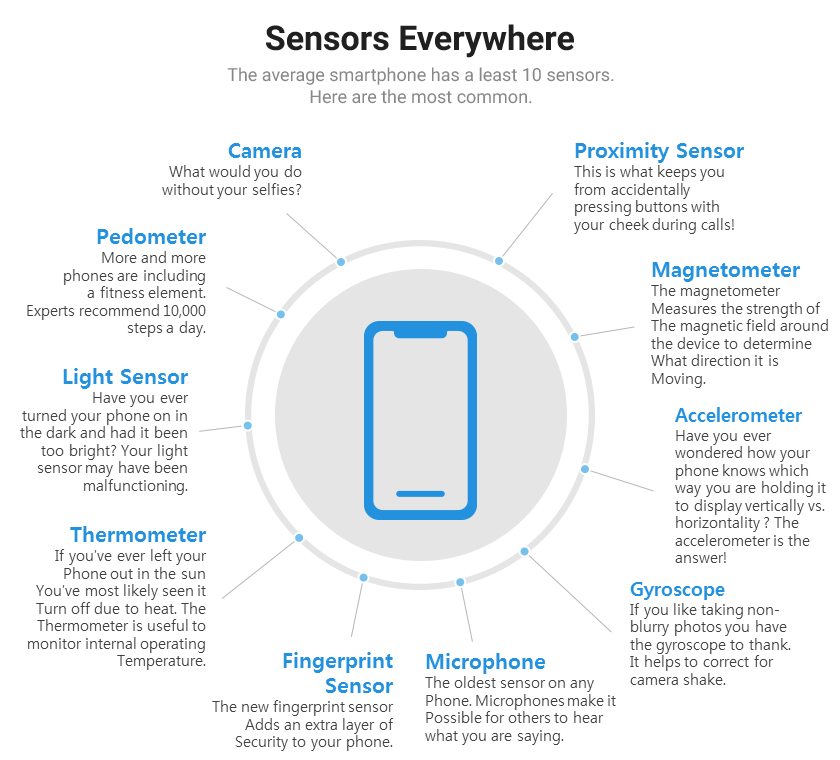
Sensor technology of Smartphone
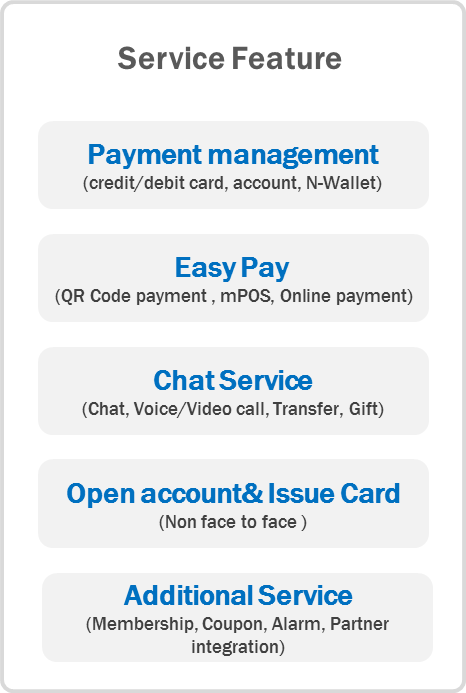
Point of sale payments for the store of the future
As a result, we can deliver the highest possible payment success rate for every transaction.
Sorry, no posts matched your criteria.


Block Chain Electronic Payment Service
The block chain trading system for mobile electronic wallet services provides a transparent and reliable trading environment for both users and merchants.
Biometrics